Stealing CSRF tokens using XSS on Signup page
I'm assuming everyone reading this blog post know what CSRF and XSS are.If you don't, having a quick search on google can yield you many results.
While crawling for vulnerabilities and searching on google, navigating through pages. I finally landed on a website. As per disclosure policies I'm not allowed to disclose the company/website. So lets use REDACTED.com.
Doing recon using passive and active techniques. I found no sub-domains , no low hanging vulnerabilities. Every mechanism works pretty fine or may be I missed something. After hours of testing, signup page caught my attention.
I was like "How did I miss this..."
Navigated to https://www.REDACTED.com/signup
After analysis, the url input fields are vulnerable to XSS. But it turns out to be useless because it's on signup page.I though of exploiting it.
First I registered an account and verified it using the confirmation link I received in my inbox.
I navigated to profile section and saw that the form to update profile content is protected with Anti-CSRF tokens.Tried different methods to bypass but no luck.
while being logged in I navigated to https://www.REDACTED.com/signup . I was presented with signup page. It didn't break my session and even did not redirect me back to dashboard , I'm in signup page and i'm not logged out.
Fishy...
So thought of exploting XSS present in signup page, but useful cookies are flagged as HTTPOnly, so couldn't grab cookies of user. Checked the CSRF token on the signup form , token on signup form and token in the profile section are SAME . :D
When user visits signup page with his account logged in, his csrf token gets injected into form of signup page.
Quickly crafted a exploit and saw it in action and it worked.
Victim logs into his account on REDACTED.com. Attacker crafts a webpage with signup form of REDATED.com and filled up the values to XSS payloads. The form is attached with a token which attacker got when attacker visited signup form.When victim visits attackers site, the form present in the attacker site gets automatically submitted. And sends victim's CSRF token to attacker.
FLOW :
Victim visits attacker's webpage---->attacker webpage with malicious form gets submitted automatically---->REDACTED.com--->Signup form with victim CSRF token is attached to the form and gets reflected on victims browser.----> Reflected page executes XSS payload and send victim CSRF token to attacker.
Finally:
Self-xss --> CSRF Token theft.
It's now fixed and got me nice bounty :D
Signing off
-Varun
Follow Me @Instagram
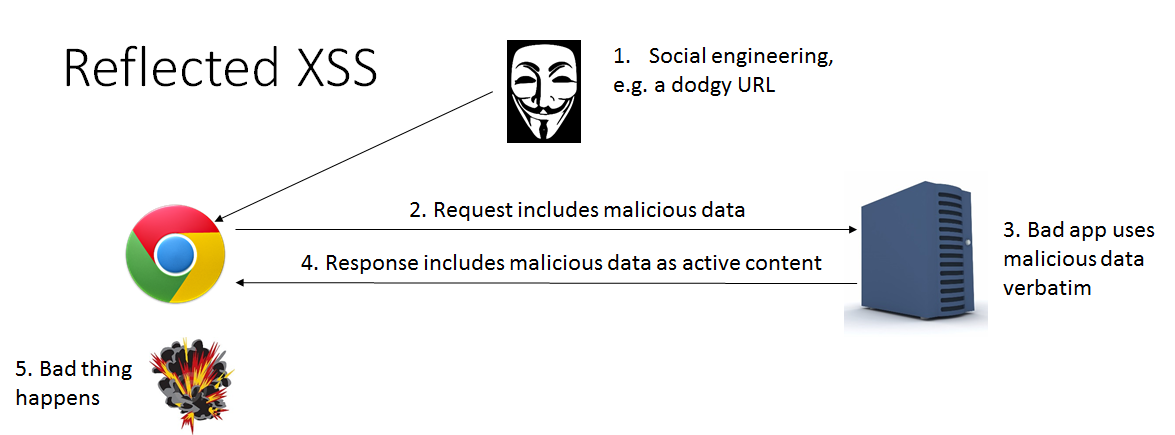 I'm assuming everyone reading this blog post know what CSRF and XSS are.If you don't, having a quick search on google can yield you many results.
I'm assuming everyone reading this blog post know what CSRF and XSS are.If you don't, having a quick search on google can yield you many results.




Comments
Post a Comment